Security Services

11:59
Security Mechanisms
15:54
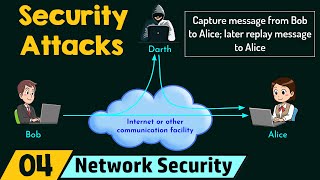
Security Attacks
16:08
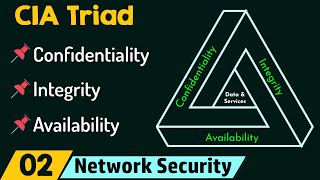
CIA Triad

13:48
How To Learn Any Skill So Fast It Feels Illegal

10:17
Introduction to Cryptography and Network Security

17:34
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)

15:45
SECURITY SERVICES IN NETWORK SECURITY || AUTHENTICATION || CONFIDENTIALITY || INFORMATION SECURITY

30:16