CIA Triad

8:41
The OSI Security Architecture
13:34
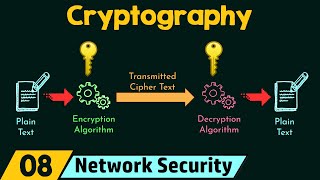
Cryptography

4:58:59
Cyber Security Full Course for Beginner

32:20
JD Vance goes after European allies in Munich Security Conference speech | DW News
24:52
The Most Useful Thing AI Has Done

4:07
What is the CIA Triad

19:20
OSI and TCP IP Models - Best Explanation

20:53