Elliptic Curve Cryptography – From useless to indispensable

8:42
Elliptic Curves - Computerphile

13:14
Master SecOC in practice - Learn to know the three major operational challenges

7:45
Curves which make Bitcoin possible.
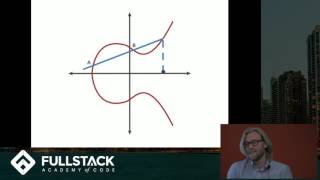
11:34
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange

12:24
Eliptik Eğri Arka Kapı - Computerphile

14:47
Cybersecurity Risk Assessment (TRA/TARA) – Why to use attack trees, and when to keep away from them?

10:08
AfD-Kanzlerkandidatin Weidel im Interview | heute journal

8:39