Security Goals in cryptography | Confidentiality | Integrity | Availability | Authentication

9:35
What is Asymmetric Key Cryptography | Elements of Asymmetric key cryptography | Asymmetric cipher

15:45
SECURITY SERVICES IN NETWORK SECURITY || AUTHENTICATION || CONFIDENTIALITY || INFORMATION SECURITY
16:08
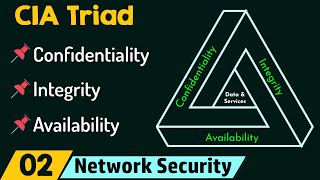
CIA Triad

16:52
Kerberos Authentication Explained | A deep dive
12:33
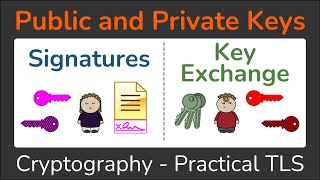
Public and Private Keys - Signatures & Key Exchanges - Cryptography - Practical TLS

11:59
Security Mechanisms

1:55:27
Worst Fails of the Year | Try Not to Laugh 💩

18:35