Playfair Cipher in network security | Playfair Cipher example | Playfair cipher encryption

6:08
Vigenere Cipher (Polyalphabetic Cipher) | Vigenere table | How to create vigenere table from Key

15:20
Hill Cipher Encryption and Decryption | Encryption and Decryption example of hill cipher

15:59
Monoalphabetic Cipher

14:05
Substitution Techniques: Playfair Cipher Explained with 2 Solved Qns Step by Step-#21is71 #vtupadhai

5:24
Columnar Transposition Cipher (Network Security) | Columnar Transposition Cipher in Network Security

17:46
#11 Playfair Cipher with Example - Encryption Techniques | Information Technology |

12:10
Playfair Cipher (Solved Question)
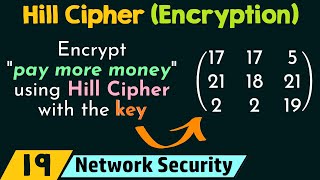
17:39