Phishing 2.0 - Detecting Evilginx, EvilnoVNC, Muraena and Modlishka
6:00
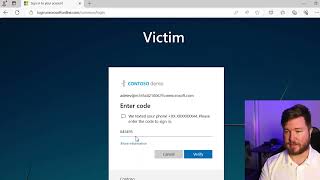
How hackers are breaking into MFA enabled Microsoft 365 accounts
51:58
Aprofundamento do proxy do aplicativo Azure AD

32:21
Smishmash - Text Based 2fa Spoofing Using OSINT, Phishing Techniques and a Burner Phone

25:40
I Took Over a Microsoft Cloud Account. Again.

45:22
Snowflake: The tip of the iceberg – Three practical takeaways from the Snowflake incident

1:22:03
What's new in the world of reverse proxy phishing?

44:07
How attackers can bypass phishing-resistant MFA | Use these protections!

31:14