Is PAM really the best choice for secure user authentication?

50:16
Linux Account Security and PAM | Into the Terminal 119

18:30
Securing Your Linux System with Advanced SSH Configuration

17:34
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)
51:56
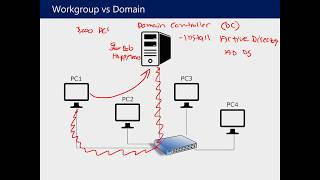
Understanding Active Directory and Group Policy

33:00
How to set up your virtual environments with Red Hat Satellite
28:51
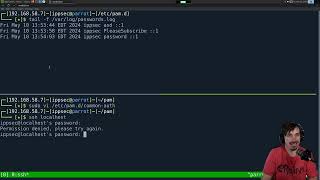
Using PAM EXEC to Log Passwords on Linux

12:46
Identity and Access Management - CompTIA Security+ SY0-701 - 4.6

9:23