Command Injection | Complete Guide

20:12
Command Injection - Lab #1 OS command injection, simple case | Long Version

1:11:53
SQL Injection | Complete Guide

47:04
Server-Side Request Forgery (SSRF) | Complete Guide

1:21:09
Introduction to OS Command Injections - Full Course

13:05
Getting Started with Command Injection

1:23:59
NMAP Full Guide (You will never ask about NMAP again) #hackers #scanning #nmap

12:16
How Hackers Bypass Firewalls?!
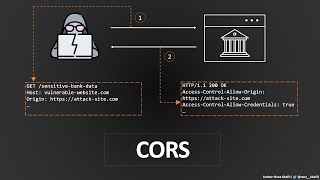
52:17