Anatomy of an Enterprise Mobile Security Incident

38:04
Attack Vectors in Orbit: The Need for IoT and Satellite Security

45:36
Webcast: In-Depth Analysis of a Phishing Email

41:05
Leading Developer Security Adoption

53:46
RSAC 365 Innovation Showcase: Identity Security in the World of AI

59:32
Evolving Threat Modeling for Agility and Business Value
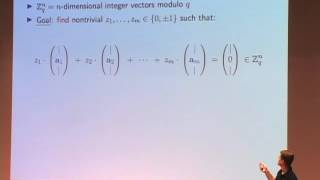
1:19:38
Chris Peikert: Lattice-Based Cryptography

35:05
Implementing Product Security Through Flexible Bill of Materials (BOM) Structure

2:01:36