A NIST 800-207 Playbook: Zero Trust from the Whiteboard to the Boardroom

32:37
MCRA Zero Trust Overview

21:31
Applying the CISA Zero Trust Maturity Model to Your Enterprise

35:00
Zenith Live 2024: Harnessing Zero Trust and AI to Outpace Cyberthreats | Zscaler

58:12
Applying Zero Trust to Operational Technology and Critical Infrastructure in the US Federal Gov.

26:48
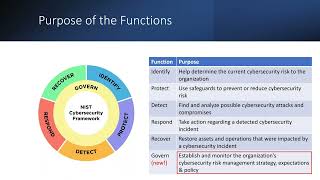
The NIST Cybersecurity Framework 4 Step Guide

45:42
Overview of Zero Trust Architectures

45:07
NIST 800-207A: Implementing Zero Trust Architecture
53:49