SECURITY SERVICES IN NETWORK SECURITY || AUTHENTICATION || CONFIDENTIALITY || INFORMATION SECURITY

30:19
SUBSTITUTION TECHNIQUES IN NETWORK SECURITY || INFORMATION SECURITY||CEASER CIPHER||PLAY FAIR CIPHER

18:03
TYPES OF ATTACKS IN NETWORK SECURITY || ACTIVE ATTACKS || PASSIVE ATTACKS || INFORMATION SECURITY

40:57
NETWORK SECURITY - TYPES OF AUTHENTICATION (Message Encryption, MAC, Hash Functions)

22:53
NETWORK SECURITY - SECURE ELECTRONIC TRANSACTION(SET) - PART 1

42:16
NETWORK SECURITY - SHA 512 (AUTHENTICATION ALGORITHM)
15:54
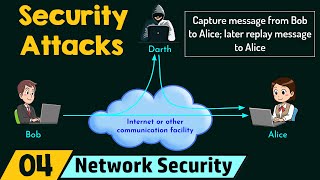
Security Attacks

17:34
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)

19:04