Indicators of Compromise #cybersecurity #cyber #learning

16:55
Cybersecurity Trends for 2025 and Beyond

38:35
How I Would Learn Cybersecurity If I Could Start Over in 2025 (Complete Roadmap & Breakdown)

17:34
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)

14:22
Protect Yourself Online: Disposable Browsing & Virtual Environments
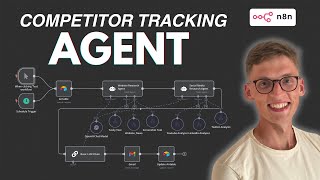
36:39
Build 24/7 Competitor Tracking Agent That Scrapes Anything (Free Template)

41:48
ChatGPT de A à Z : Le cours complet

8:05
ZTNA - Zero Trust Network Access Explained! #cybersecurity #cyber #zerotrust #zerotrustsecurity

19:00