Broken Access Control | Complete Guide

16:33
Broken Access Control - Lab #1 Unprotected admin functionality | Long Version
52:17
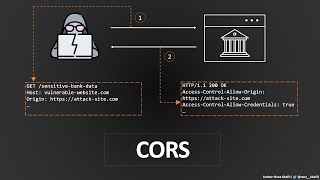
Cross-Origin Resource Sharing (CORS) | Complete Guide

10:35
2021 OWASP Top Ten: Broken Access Control

22:33
Directory Traversal | Complete Guide

1:11:53
SQL Injection | Complete Guide

31:46
"Easiest" Beginner Bugs? Access Control and IDORs

12:04
What is Broken Access Control?

47:04