Breaking The Kill Chain: A Defensive Approach

14:04
ATT&CK Matrix: The Enemies Playbook

13:39
Cyber Kill Chain | Cyber Kill Chain Explain | What is Cyber Kill Chain? Kill Chain | Cybersecurity

31:15
Cybersecurity Architecture: Who Are You? Identity and Access Management

8:54
What is XDR vs EDR vs MDR? Breaking down Extended Detection and Response

14:55
Real Hacking: Learn The Cyber Kill Chain
7:44
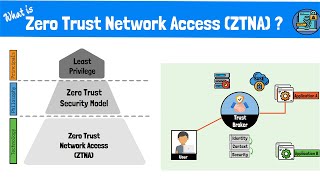
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies Explained

1:18:10
License to Kill: Malware Hunting with the Sysinternals Tools

42:16