1. Introduction, Threat Models

1:27:39
2. Control Hijacking Attacks

1:18:26
12. Network Security

1:09:05
Internet Networks & Network Security | Google Cybersecurity Certificate

1:00:21
1. Introduction and Matrix Multiplication
1:25:07
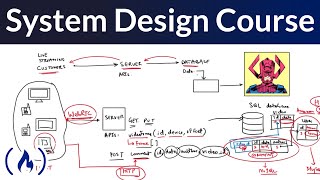
System Design for Beginners Course

4:58:59
Cyber Security Full Course for Beginner
24:52
The Most Useful Thing AI Has Ever Done

1:22:49