What is the CIA Triad

12:34
Cybersecurity Architecture: Fundamentals of Confidentiality, Integrity, and Availability

17:34
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)

27:14
Transformers (how LLMs work) explained visually | DL5
16:08
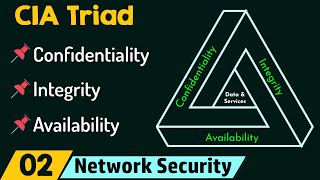
CIA Triad

8:33
FBI vs CIA - How Do They Compare?

8:27
Building a Cybersecurity Framework

27:31
Cybersecurity Architecture: Networks

36:55