Using Undocumented CPU Behavior to See Into Kernel Mode and Break KASLR in the Process

50:27
Breaking Kernel Address Space Layout Randomization (KASLR) With Intel TSX

22:32
USENIX Security '18 - Meltdown: Reading Kernel Memory from User Space

38:21
Breaking FIDO: Are Exploits in There?

23:49
Side-Channel Attacks on Everyday Applications

47:39
Demystifying the Secure Enclave Processor

50:29
Using An Expanded Cyber Kill Chain Model to Increase Attack Resiliency
26:25
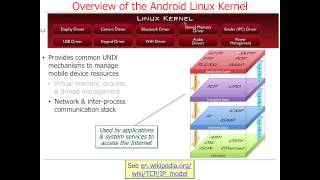
Overview of Android Layers (Part 1)

46:34