Top 12 Tips For API Security
5:48
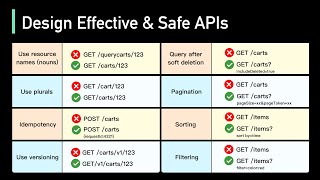
Good APIs Vs Bad APIs: 7 Tips for API Design

6:12
API Authentication: JWT, OAuth2, and More

17:34
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)

1:49:04
API Security Fundamentals – Course for Beginners

5:51
API Authentication Simplified: Secure Your APIs in 5 Minutes!

13:19
Proxy vs Reverse Proxy vs Load Balancer | Simply Explained

11:16
What Is an API? | API Security Explained | API Security Best Practices | Simplilearn

6:05