Symmetric Key Distribution using Symmetric Encryption | Key Distribution

7:16
Symmetric Key Distribution using Asymmetric Encryption | Key Distribution

15:44
Public Key Distribution in Cryptography | Public Key Distribution | Key Distribution

6:57
Key Management and Key Distribution in Cryptography | Key Management | Key Distribution
5:54
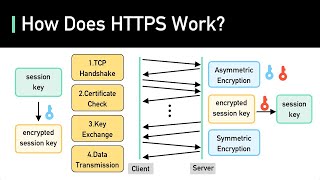
SSL, TLS, HTTPS Explained

11:49
Explaining the Diffie-Hellman Key Exchange
12:33
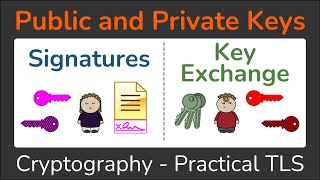
Public and Private Keys - Signatures & Key Exchanges - Cryptography - Practical TLS

21:42
Remote User Authentication: Principles & Techniques | Cryptography- #21is71 #cryptography #vtupadhai
18:50