LLM Agents for Vulnerability Identification and Verification of CVEs

29:34
End-to-End Framework using LLMs for Technique Identification and Threat-Actor Attribution
29:11
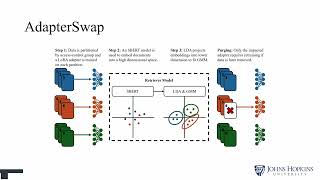
AdapterSwap: Continuous Training of LLMs with Data Removal and Access-Control Guarantees

26:07
Towards Autonomous Cyber-Defence: Using Co-Operative Decision Making for Cybersecurity

28:24
Structure and Semantics-Aware Malware Classification with Vision Transformers

56:37
Case Study: Horizontal scaling in PAS for OpenEdge - PUG CHALLENGE 2024

1:07:59
Keynote - Acting to Ensure AI Benefits Cyber Defense in a Decade of Technological Surprise
19:49
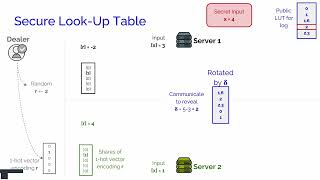
Curl: Private LLMs through Wavelet-Encoded Look-Up Tables
26:16