Kubernetes Hacking: From Weak Applications to Cluster Control

24:05
they tried to hack me so i confronted them

22:41
Hacking CI/CD (Basic Pipeline Poisoning)

28:53
Kubernetes Security Best Practices - Ian Lewis, Google

2:01:46
Hacking Web Apps, Kubernetes, and More! - (Pwned Labs)

33:45
How To Pivot Through a Network with Chisel

19:49
Talos OS - Taking the Sting Out of Kubernetes Deployments

17:38
What SECRETS are in your Clipboard?
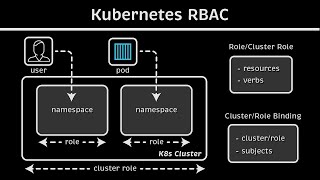
23:17