How to Use MITRE ATT&CK Framework Detailed Approach 2022

14:11
Preguntas y respuestas de la entrevista SOC 2 2022

35:48
Introduction To The MITRE ATT&CK Framework

50:42
MITRE's ATT&CK framework - De la Teoría a la Práctica | Seguridad Cero
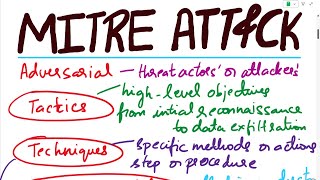
16:43
MITRE ATTACK | MITRE ATT&CK | MITRE ATT&CK Explained with an Example | MITRE ATT&CK Analysis

48:05
Qué es un SIEM, cómo funciona y casos de uso

1:47:11
Workshop: MITRE ATT&CK Fundamentals

1:55:43
The Best of Ludovico Einaudi | Greatest Hits 2024 | [2 HOURS]

42:16