Hill Cipher Encryption and Decryption with Numerical | Everything about Hill Cipher

16:34
Rail Fence and Row Transposition cipher techniques | Types Of Transposition Techniques

21:58
HILL CIPHER 3X3 Matrix Example Encryption and decryption

30:03
Hill Cipher (Decryption)

26:30
AES Algorithm in Hindi | Advanced Encryption Standard Algorithm in Cryptography & Network Security

8:54
Germany’s Far-Right Comeback | NYT Opinion

12:28
Playfair Cipher Algorithm
17:39
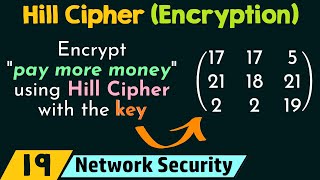
Hill Cipher (Encryption)

14:32