9-3 BB84 Protocol

7:15
9-4 Eavesdropper detection

17:31
How Quantum Computers Break Encryption | Shor's Algorithm Explained

17:15
Why Quantum Computing Requires Quantum Cryptography

12:41
How Quantum Key Distribution Works (BB84 & E91)

17:46
Quantum Entanglement Explained for Beginners | Physics Concepts Made Easy
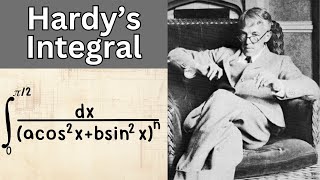
13:47
Hardy's Integral

21:53
28.Quantum key distribution I: BB84 protocol

15:09