17. User Authentication

1:20:13
18. Private Browsing
50:26
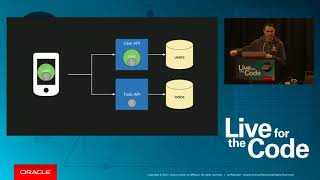
Authentication as a Microservice

1:18:26
12. Network Security

1:17:13
1. Introduction, Threat Models

17:13
Auth Does NOT Have To Be Hard

16:52
Kerberos Authentication Explained | A deep dive

1:17:25
23. Security Economics

1:02:17