Workshop: Building Your Risk-Oriented Application Security Program

35:48
Learn Nuclei in 30 minutes - DEF CON Nuclei Demo
34:41
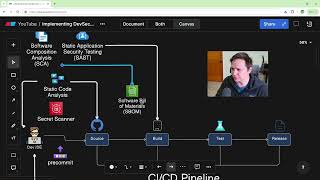
How to Create a DevSecOps CI/CD Pipeline

47:21
The Bug Hunter's Methodology - Application Analysis | Jason Haddix

19:47
Is AI Saving or Taking Jobs? Cybersecurity & Automation Impact

53:46
Tackling SAP Security Together – Building a Robust SAP SOC Framework

8:53
Application Security 101: A Simple Guide

8:52
Installing tools with PDTM | Getting started Part 2

22:40