The Anatomy of an Att&ck
13:18
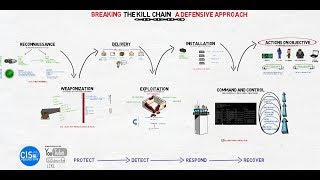
Breaking The Kill Chain: A Defensive Approach

35:48
Introduction To The MITRE ATT&CK Framework

8:40
Anatomy of an AI ATTACK: MITRE ATLAS

13:48
How To Learn Any Skill So Fast It Feels Illegal

17:34
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)
16:43
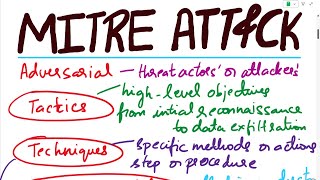
MITRE ATTACK | MITRE ATT&CK | MITRE ATT&CK Explained with an Example | MITRE ATT&CK Analysis

14:54
Claude 3.7 Sonnet Just Shocked Everyone! (Claude 3.7 Sonnet and Claude Code)

30:21