Password Hacking in Kali Linux

16:55
Hacking Complex Passwords with Rules & Munging

22:12
3 Levels of WiFi Hacking

20:01
How Hackers Move Through Networks (with Ligolo)

16:59
Find Information from a Phone Number Using OSINT Tools [Tutorial]
19:57
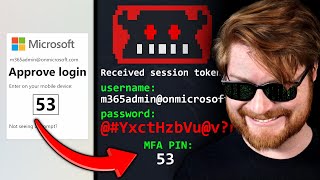
I Stole a Microsoft 365 Account. Here's How.
18:21
How to HACK Website Login Pages | Brute Forcing with Hydra

16:37
You will never ask about Kali Linux again! (Full guide about Kali Linux)

41:06