How attackers can bypass phishing-resistant MFA | Use these protections!

48:49
The strongest form of MFA? | Why your MFA may need an upgrade

36:32
Manage Local Admin Accounts Securely | Top Tips

37:05
Secure Your Devices with Defender for Endpoint - Part 1

1:10:42
PASSKEYS - What they are, why we want them and how to use them!

39:50
The Tech Behind Mile High Dreamin'. Chris Fellure and Paul Fox
6:00
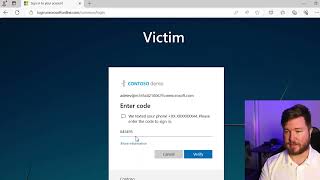
How hackers are breaking into MFA enabled Microsoft 365 accounts

33:49
Share Documents Securely | SharePoint

35:54