Finding Vulnerabilities through Static Analysis and Scripting

1:27:01
OWASP API Security Top 10 Course – Secure Your Web Apps

1:24
Feature Overview: Verified stolen credential detection

45:33
Lookin’ for Bugs in All the Wrong Places
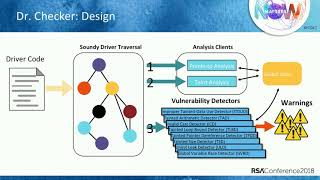
44:41
How Automated Vulnerability Analysis Discovered Hundreds of Android 0-days

47:21
The Bug Hunter's Methodology - Application Analysis | Jason Haddix

2:12:41
Binary Exploitation Deep Dive: Return to LIBC (with Matt)

48:23
Journey Through Postgres, Exploring the Elephant

55:39