Defending Against Indirect Prompt Injection Attacks With Spotlighting

29:34
End-to-End Framework using LLMs for Technique Identification and Threat-Actor Attribution

1:10:56
Prof. Tulika Mitra on Embedded Heterogeneous Computing: An IEEE CS SCV Chapter Event

1:05:48
Stanford Seminar - Electronic Design Automation and the Resurgence of Chip Design
29:11
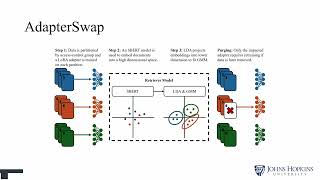
AdapterSwap: Continuous Training of LLMs with Data Removal and Access-Control Guarantees

26:07
Towards Autonomous Cyber-Defence: Using Co-Operative Decision Making for Cybersecurity

20:33
PyRIT: A Framework for Security Risk Identification and Red Teaming in Generative AI Systems

35:36
Nach der Wahl: Scholz tritt ab, Merz übernimmt, die AfD verdoppelt sich | heute-show vom 28.02.2025
25:39