DEF CON 32 - Gotta Cache ‘em all bending the rules of web cache exploitation - Martin Doyhenard

38:14
DEF CON 32 - SQL Injection Isn't Dead Smuggling Queries at the Protocol Level - Paul Gerste

42:37
DEF CON 32 - Listen to the Whispers: Web Timing Attacks that Actually Work - James Kettle

6:15
How to make Reticulum Network Stack rnsd Start on Boot on Linux
43:55
Practical Web Cache Poisoning: Redefining 'Unexploitable'

32:30
DEF CON 32 - The Darkest Side of Bug Bounty - Jason Haddix

11:24
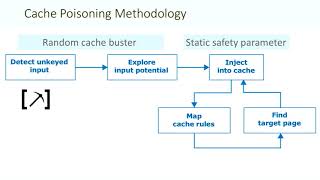
Web Cache Poisoning: Hunting Methodology & Real-World Examples

42:55
DEF CON 32 - Counter Deception: Defending Yourself in a World Full of Lies - Tom Cross, Greg Conti

27:22