Implementing Zero Trust at Microsoft

21:06
Transforming the employee experience with a Zero Trust strategy

51:54
What We Learned Implementing Zero Trust Security at Microsoft

57:11
Understanding and Getting Started with ZERO TRUST

17:59
Cybersecurity and Zero Trust

30:51
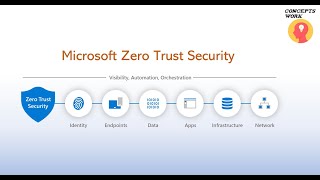
How Microsoft does Zero Trust

30:14
AMD, Don't Screw This Up

45:42
Overview of Zero Trust Architectures
29:16