How CPUs Access Hardware - Another SerenityOS Exploit

19:02
Reading Kernel Source Code - Analysis of an Exploit

22:13
The Circle of Unfixable Security Issues

15:46
I Designed My Own 16-bit CPU

15:23
Kernel Root Exploit via a ptrace() and execve() Race Condition
14:05
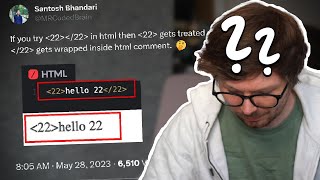
Generic HTML Sanitizer Bypass Investigation

51:00
GOD MODE UNLOCKED - Hardware Backdoors in x86 CPUs
13:24
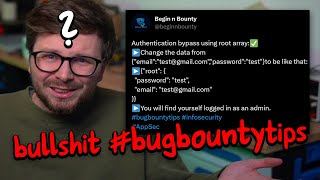
Authentication Bypass Using Root Array

7:43