SHA: Secure Hashing Algorithm - Computerphile

8:12
Hashing Algorithms and Security - Computerphile
19:38
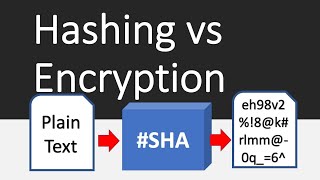
Hashing vs Encryption Differences

17:30
Running a Buffer Overflow Attack - Computerphile

9:24
Securing Stream Ciphers (HMAC) - Computerphile

6:03
Hashing and Hashing Algorithms - md5 sha1 sha256 sha2 sha3 - Cryptography Essentials

5:59
The unsolved math problem which could be worth a billion dollars.

9:11
One Encryption Standard to Rule Them All! - Computerphile

14:14